Cybersecurity Awareness Month has come and gone, but we would be remiss without addressing Incident Response. Before we do, let’s recap the ground we’ve covered in the first four of five installments on a robust Cybersecurity and Data Privacy Program.
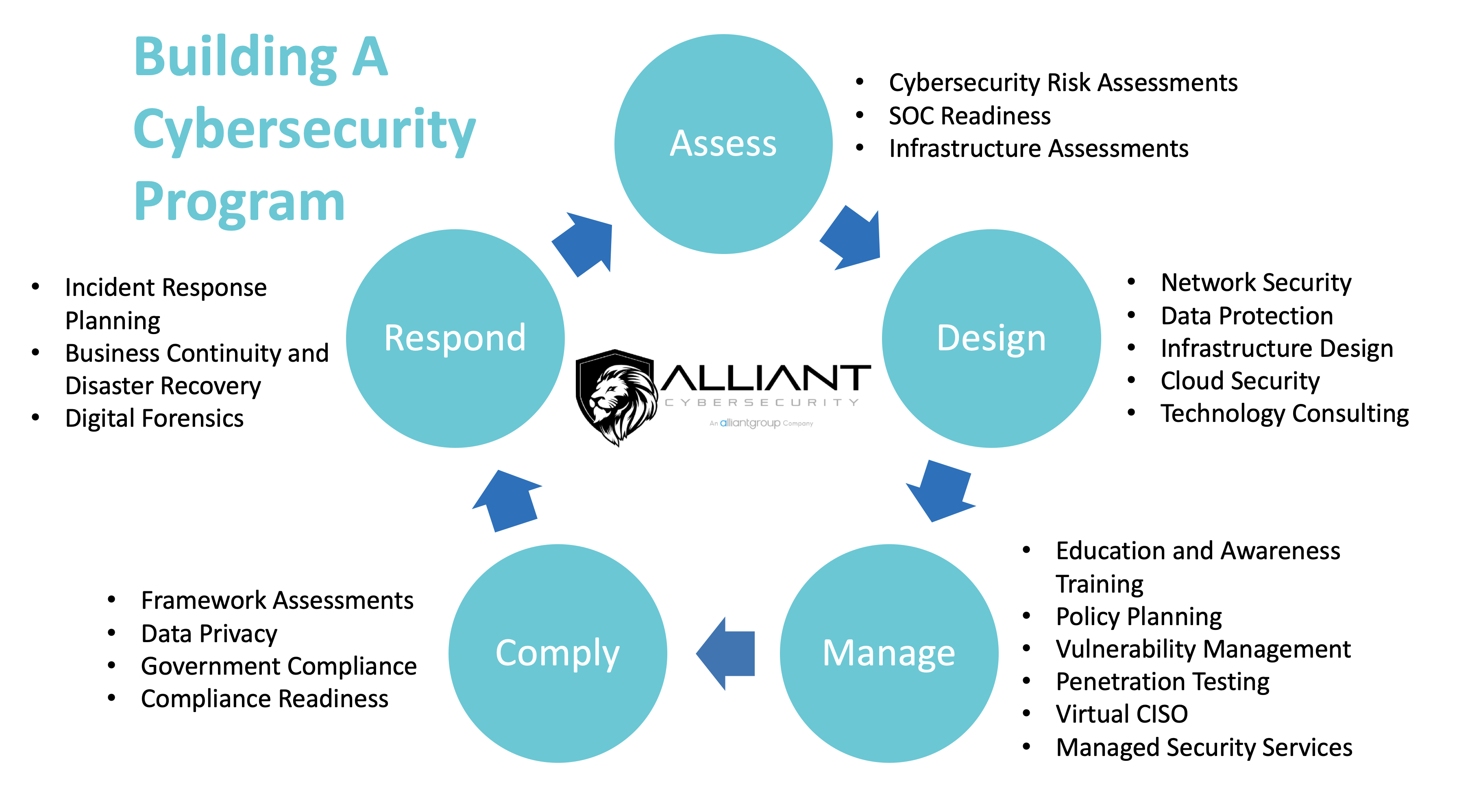
- Conduct an Assessment. Taking stock of your Strengths, Weaknesses, Opportunities, and Threats from a holistic viewpoint of People, Process, and Technology using a recognizedframework should help determine your risk appetite and give you that vital roadmap to start improving.

- Incorporate Data Privacy and Cybersecurity by design into your organization. Start at the beginning of each major project and aspect of the business rather than hurriedly bolting them on as an afterthought. It is lessexpensive, and the controls will generally be less invasive and still more effective. A knowledgeable and experienced Security Architect is a must for this phase.
- Implement controls and metrics to Manage those controls around Data Privacy and Cybersecurity. These are the means by which organizations improve their risk management posture.
- Include both Security and Compliance; related but not the same. Compliance is about adequately meeting stated governance and control requirements from an external entity. Think CCPA, GLBA, PCI-DSS, SOX, CMMC, GDPR, etc.
The impacts of cyber incidents reflected in the graphic at the top of this article are staggering and only getting more alarming by the day. Incidents could include, but may not be limited to:
- a significant data loss,
- inability to access data for any number of reasons – natural or human-made,
- a data “breach”,
- extortion,
- loss of a portable device,
- theft of data,
- unauthorized manipulation of data, or
- inappropriate release of data.
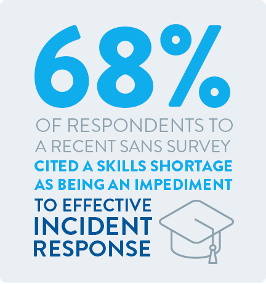
It is not a matter of if, but when you will be impacted by a cyber event/incident of some form or another. The extent of the adverse impact from that event is almost completely dependent upon your organization’s pre-planning, preparation, and training for this inevitability. Between double extortion ransomware events, executive email compromise, and now governments enforcing penalties if you acquiesce to the cybercriminals, the stakes have not been higher. Further complicating the issue is the lack of skilled resources available to help you respond, as the SANS survey sighted here shows. Having a value-adding partner like Alliant can be a tremendous bolster to your program.
Incident Response should be part of your holistic Business Continuity efforts. A robust program typically consists of three parts (some models have as many as six), PREPARE, RESPOND, RECOVER. Most importantly, Incident Response should begin long before any waste matter hits the rotary oscillator!
Prepare – You think about and prepare for the types of events that could befall your organization. Besides a direct attack on your organization like Denial of Service, Email Compromise, or Ransomware, you should also consider things like key members of your supply chain getting compromised, insider threat, data privacy violation allegations, etc. In a recent LinkedIn article (https://www.linkedin.com/pulse/questions-answered-smbs-dealing-cybersecurity-incident-jon-murphy) we go into greater detail of industry-specific examples to consider. You write up a plan document that envisions these scenarios, then you train, exercise, and improve it, at least annually.
Detect & Respond – You must have the capability in place to rapidly detect the event and timely respond to mitigate further damage. All too often, organizations have been infiltrated months ago (called dwell time) and only discover the compromise when law enforcement, a supplier, or worse yet, a client informs them. Detect and respond requires the right combination of people, process, and technology to already be in place. Managed Detection and Response (MDR) with Security Operations Center as a Service (SCOaaS) is a huge lift here on the technology front. Though integral, the people part of the equation involves more than just calling on your Managed Services Provider (MSP) or internal IT people.
Depending on the circumstances, people could likely involve outside experts (all of whom should already be on retainer) like a digital forensics firm, specialized outside counsel, a crisis communication firm to handle customer, press, and authority inquiries, and your cyber liability insurance provider. Each of these relationships should be well established prior to any event, rather than sourced via a frantic web search post-incident discovery.
Recover – The last part is getting back to some form of business-as-usual (BAU), or better stated, a new normal. This means while the event is still fresh in everyone’s minds, conducting a thorough and objective post-mortem on what happened, how it happened, and if possible, why. Then use those lessons learned to make the needed improvements. These improvements can be to people (e.g., training, hiring), process (e.g., better vendor oversight, more stringent policies), or better technology (e.g., Intrusion Detection, MDR) or any combination thereof. It will also likely call for substantial damage control measures with your clients, suppliers, and possibly regulators – depending on your industry. With “breaches” and data privacy violations, there are extensive, time-constrained legal notification requirements in many jurisdictions. An outside expert will likely be required to manage the notification aspects alone.
We hope you never have to enter the latter part of the Incident Response stages of your security program – Respond and Recover. You can probably tell that these two latter stages are the most expensive parts of the whole program, especially with little to no pre-need research and planning. In fact, in our experience, we see all the other earlier elements in the program, done with skill and foresight, can be five to ten times less expensive than enduring just one instance of the full response and recovery elements alone. Furthermore, if you have adequately implemented those other four earlier program elements, Assess, Design, Manage, Compliance, you are less likely to be compromised in the first place, and the impacts are far more manageable! In other words, the old adage of “an ounce of planning is worth a pound of cure” once again holds true here too.
In summary, regarding Incident Response, organizations should:
- Determine what likely events/incidents (and maybe not so likely. For instance – how many organizations had a pandemic plan before COVID-19 hit?) could befall their organization. Create a comprehensive, tailored plan for your organization, train, and exercise on it at least
- Implement the tailored plan in response, adapting as exigencies arise, and calling on all the partners within the plan to help stop the damage.
- Recover to BAU in the new normal state.
Thank you for reading our series, and we sincerely hope the content has made you better informed. Please call on us if we can answer any questions that we may have brought to light. In the meantime,
BE AWARE. BE SECURE.